- Business Process Management (BPM)Document Management System (DMS)Electronic Quality Management System (QMS)Risk, Governance & Compliance (GRC)Low Code Rapid Application Development (LC)Business Continuity Management (BCM)Enterprise Architecture (EA)Business Process Management (BPM)Document Management System (DMS)
- Document Control Overview
- AI Content Creation & Improvement
- Policy & Procedure Management (SOP)
- AI Content Mining Parser
- Collaboration & Governance
- Data Migration & Integration
- Interfacing Offline App
 Electronic Quality Management System (QMS)
Electronic Quality Management System (QMS)- Quality Management System Overview
- Document Control & Records Management
- Audit & Accreditation Management
- Corrective & Preventative Action
- Quality Event (Non-conformity / Complaint/ Compliance)
- Risk Management
- Incident Management
- Environmental Health & Safety
- Product & Supplier Management (SCAR)
- Training Management
- Control Management
- Action Items Management
- Management Review
- FMEA
- Pharmacovigilance
- Data Migration & Integration
 Risk, Governance & Compliance (GRC)
Risk, Governance & Compliance (GRC)- Risk, Governance & Compliance Overview
- Risk & Control Management
- Regulatory Compliance
- Collaboration & Governance
- Data Migration & Integration
- Interfacing Offline App
 Low Code Rapid Application Development (LC)
Low Code Rapid Application Development (LC)- Low Code Automation Platform Overview
- Electronic Web Form Design (eFORMS)
- Database Table Entity Designer
- System Integration Designer
- Design & Manage Tasks
- Design & Manage BPMS Apps
- Custom Rules/Guards/Actions
- Electronic Services
- User Homepage
- BAM (Business Activity Monitoring)
- Custom Dashboard Design
- Data Migration & Integration
 Business Continuity Management (BCM)
Business Continuity Management (BCM)- Business Continuity Management Overview
- Business Impact Analysis
- Disaster Recovery Simulation
- Action Item Management
- Mass Notification Management
- Asset Management
- Interfacing Offline App
 Enterprise Architecture (EA)
Enterprise Architecture (EA) - IndustriesRegulatory ComplianceUse CasesLearning CenterFramework & PracticesIndustries
- Healthcare
- Medical Device Technology
- Life Science, Pharmaceutical
- Aerospace & Defense
- Airlines and Aviation
- Media & Telecommunications
- Government and Military
- Technology
- Energy
- Logistics & Port Operations
- Banking & Capital Markets
- Retail & Consumer
- Consulting
- Education
- Engineering & Construction
- Manufacturing
- Financial Services
- Insurance
- Chemicals
Regulatory Compliance- Regulatory Compliance
- ISO
- ISO 9001 (guide)
- ISO 9001:2026 (preparation)
- ISO 17025
- ISO 27000
- ISO 27001
- ISO27002
- ISO 42001
- EU AI Act
- SOC 2 Type 1 & 2
- Sarbanes Oxley
- GxP
- GRC
- Basel
- Digital Signature
- GDPR
- IFRS
- NIST SP 800-53
 Use Cases
Use Cases- Quality Management System (QMS)
- Digital Transformation
- Continuous Improvement
- Governance, Risk & Compliance
- Knowledge Management
- System Deployment (ERP, CRM…)
 Learning CenterFramework & Practices
Learning CenterFramework & Practices - AboutCustomer SuccessPartners

ISO/IEC 27000
Please Select contact form.
ISO 27000 Series of standards: globally recognized frameworks for best practice information security management

Background of ISO 27000
During the past few decades of the digital era we have benefited greatly from the exposure to various information networks, especially the global Internet. However, as cyber-attacks became the norm and more organizations suffered from information system breaches, we came to the realization that information security needed to be taken more seriously than ever before.
Not only cyber-attacks have raised governmental level security concerns on global scale, they also became the sticking point of digital transformation for organizations, especially for those dealing with taxes, finances, sensitive personal information, as well as other critical data. Businesses nowadays need to start focusing on information security, and pave their way to success by protecting data from any breach, misuse or theft.
One common misconception is that the scope of information security is only limited to computer systems and digital data storage. Nonetheless, the depth and breadth of information security are much larger than that, and are often left unaddressed in many organizations’ risk assessment processes and risk management frameworks. That is why many companies often skip the elaboration and documentation of their data policies, including data collection, storage, distribution, sharing and disclosure policies.
Fortunately, ISO 27000 recognizes these potential issues, and provides effective control mechanisms to overcome and mitigate them.
ISO 27000 at a Glance
ISO 27000 is a series of standards that were designed to safeguard organizations’ information assets. ISO 27000 also gives an overview of an Information Security Management System (ISMS), defining and describing the logically organized set of processes that guide organizations to align their business goals and objectives with their information security.
More precisely, ISO 27000 guides organizations throughout their information security risk management, from formulation-to-execution, supervision, adjustment, evaluation and maintenance, to ensure that sensitive information assets (e.g. financial, intellectual, personal and behavioral data) are secured whether they are first-hand or secondary data.


Why ISO 27000?
Information security risk management is inevitable given the fact that there are thousands of security threats every day to your information systems. Faced with potential financial and reputational loss caused by cyber-attacks, organizations need to keep a wary eye on all the known and unknown risks – if you have never been attacked before, it does not mean that you cannot or will never become a victim.
ISO 27000 can bring peace of mind by raising information security awareness, introducing effective and trustworthy measures and fostering a culture of security. With the help of ISO 27000, management will have more confidence when optimizing their information security reserves towards business goals. Being ISO 27000 certified will also improve an organization’s overall quality, as well as portray a positive corporate image and business etiquette.


ISO 27000 Compliance Challenge
Although ISO 27000 is very comprehensive with quite straight-forward applicability, organizations still have some major difficulties when implementing ISMS due to the ever-evolving global environment. Following are some of those challenges which are worth mentioning:

Pervasive
Network Systems
Technology has immersed into almost every part of our personal and professional life, and it is inevitable for us now to provide information through wireless portable devices allowing multiple access points. The omnipresence of network systems increases vulnerability of our information security. Educating people on the potential danger and securing ubiquitous networks can be quite challenging.

Insufficient
Knowledgeable Workforce
Since ISMS is a very sophisticated and niche knowledge domain, organizations are faced with the challenge of finding competent human capital resources in the labor market, as well as the challenge of upskilling their existing workforce in order to meet the requirements of ISMS. Cultivating talent with solid basic technological knowledge followed by a comprehensive understanding of information security systems, hands-on practices and substantial rational thinking requires tremendous investments of time and money.

Conventional
E-Commerce Practices
Almost all current E-commerce platforms were built on the principle of collecting geolocation and behavioral data of customers. Such personal information can easily become the target for financial crime and hence raise huge risks to businesses and individuals. Protecting such huge amount of data in the CRM while storing new data transferred every second over the Internet needs bullet-proof information security solutions.

Emergent Information
Security Discipline
Information security is still a new and progressing field. As we recognized its importance and implications, we have been un-learning and re-learning its evolving discipline. The overall knowledge, including basics, frameworks and tactics, related to information security is still developing and far from reaching its stability and maturity.

Enterprise Risk
Management Complexity
Risk appetites can vary greatly, according to different business models, locations, target markets, scales and types of organizations. That being said, organizations might have complete different risk evaluations, hence different risk management initiatives towards the exact same risk. Even within an organization, formulating a 360-degree enterprise risk management plan covering all possible risks is difficult, because it is tricky to classify and prioritize all the risks with different scopes, intensities, severities and impacts.

Changing
Regulatory Landscape
The increasing cyber-attacks have alerted governments and organizations to make new directives, regulations, laws, rules, policies and requirements (e.g. GDPR, FTC, HIPAA, etc.) spanning private and public sectors including finance, education, medical, retails… Businesses not only need to keep pace with these regulations which keep changing and growing, but also need to follow different laws or regulations applicable across different regions. Such geopolitical challenge requires more strategic approach when complying with corporate compliance related to Information security.
ISO 27000 & our Integrated Management System (IMS) solution
Interfacing’s Integrated Management System (IMS) solution incorporates, QMS (Quality Management System) SOP (standard operating procedure), Risk management, compliance and audit, BCM (business continuity management), MDM (master data management) and other frameworks and solutions aiming at continuous improvement and digital transformation of an organization. IMS touches every aspect of ISMS while supporting business and compliance goals.
Our innovative IMS solution offers added strength to ISO 27000 over process control. Using IMS to pinpoint vulnerabilities of information security systems throughout processes can help organizations evaluate their risks in a more precise and systematic manner, formulate an all-around risk management plan, identify all critical steps and responsible personnel for implementation, and generate accurate audit trails throughout the data lifecycle.
Some prominent benefits of using Interfacing’s Integrated Management System for ISMS are:
Quality Improvement
IMS helps organizations streamline and optimize processes, draw interdependencies between processes, resources, roles, rules, risks and controls, and visualize real-time data in an intuitive and user-friendly interface. Monitoring your performance and controlling your information security can be achieved through customized widgets, dashboards and reports embedded in the Integrated Management System platform. Moreover, IMS facilitates implementation of other best practice frameworks, whether they are related or unrelated to ISMS, to support organizations’ continuous improvement management.
Agile Change Management
Traditional risk management methodology focuses on structure and system rigidness, while Interfacing’s IMS software platform adopts a SaaS model that can be implemented and rolled out in stages. As regulations, laws and policies regarding information security evolve on a daily basis, organizations are obliged to take instant action to attest compliance. IMS helps ISMS absorb and implement changes using an agile approach to accelerate change initiatives and minimize impacts followed by changes.
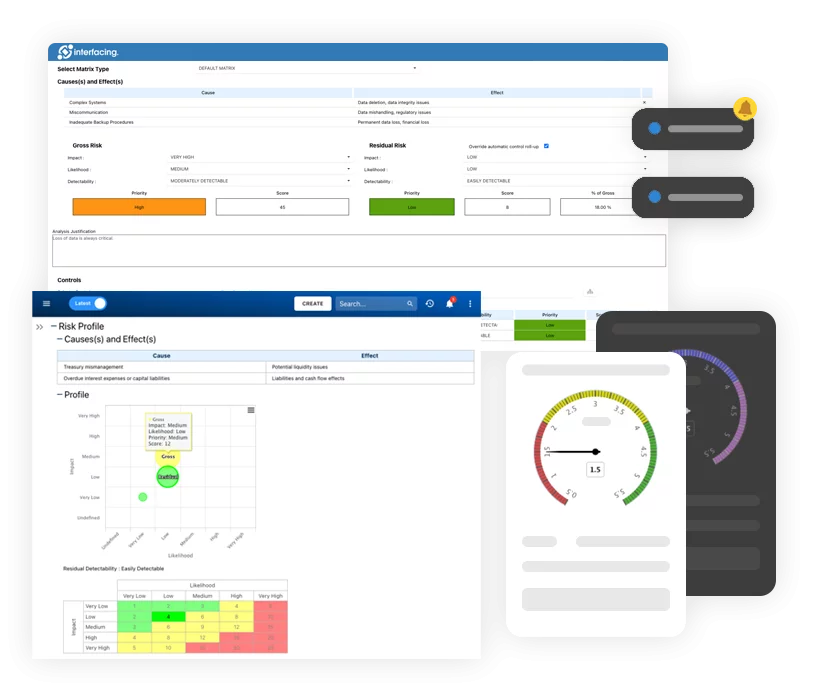
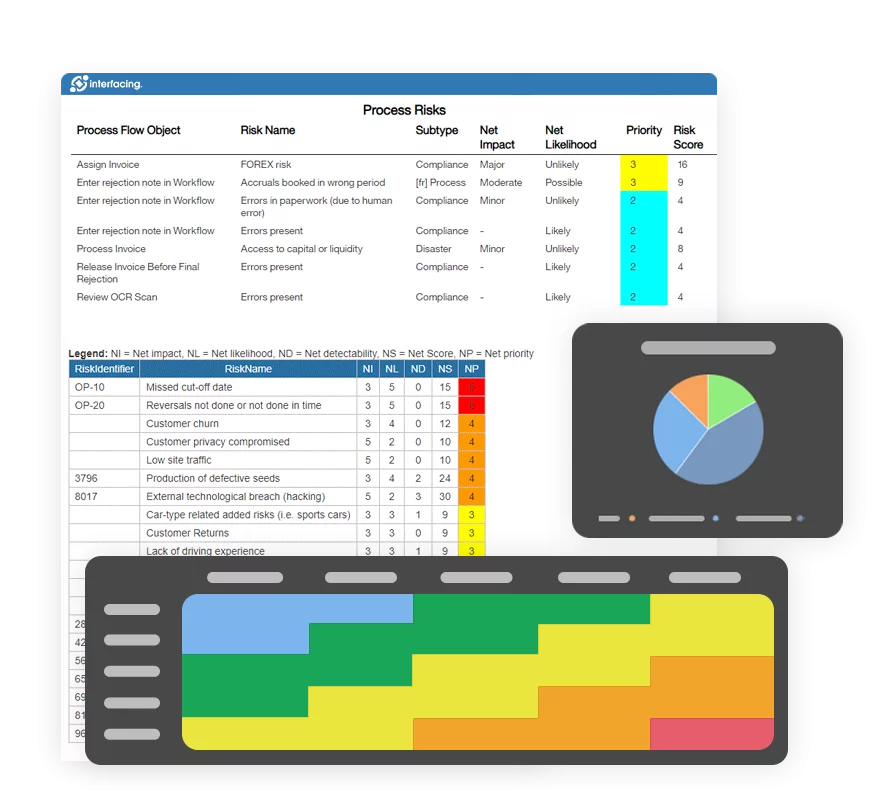
Comprehensive Risks & Controls
IMS empowers organizations to be more proactive when it comes to risk management. It supports a complete risk management lifecycle from risk identification, assessment, prioritization, association of controls and planning mitigations. Our Digital Integrated Management System solution can dynamically visualize risks in different graphs and matrices, generate risk analysis and reports, and facilitate internal and external audit efforts.
Data Stewardship
With integration capabilities with third party systems, Our Integrated Management System solution is capable of creating a single source of truth for your centralized data reference and data lifecycle management. A unified and inclusive Digital Integration platform ensures data ownership, integrity and consistency across departments. Organizing your data in a standardized way in return plays a pivotal role in strengthening your information security.
Cross-departmental Collaboration
An Integrated Management System (IMS) solution, with one common repository, allows employees to access knowledge and share best practices based on roles. Setting different security levels enable organizations to engage all internal and external stakeholders to collaborate on the same processes or tasks without sacrificing information security. Sharing information, raising improvement requests and getting notifications directly within the IMS platform further reduces collaboration frictions, especially for teams located in different locations or using different devices.
Bottom-line Empowerment
Leveraging BPM for process optimization and information security controls at the same time proves to be more cost-effective by expanding organizational IT ecosystem. This creates greater value and maximizes ROIs in the long term. Using one solution for various initiatives can also drive synergies across different programs by facilitating monitoring and reporting.
ISO 27000 & SOC2
ISO 27001 is a global standard defining all requirements and controls related to the systematic preservation and protection of information. This standard applies to all organizations of any size and industry. ISO 27001 is comprised of 114 security controls and 10 clauses that are grouped into 14 sections. Specifically, the ISMS (Information Security Management System) defined in the clauses (4 to 10), gives an organization the ability to keep its levels of security in alignment with its ability to meet the desired objectives and outcomes of its business based on a risk management approach.
Using ISO 27001 as your company’s security management foundation, in effect means that your organization is already performing many of the activities required to achieve a successful SOC 2 audit and certification.
ISO 27001 and SOC 2 working together
We shouldn’t be asking which of the two frameworks to use simply because SOC 2 is an audit report while ISO 27001 was designed as a standards certification established to create a specific Information Security Management System. This means that SOC 2 can be seen as an output brought on by the delivery of an ISO 27001 ISMS implementation.The relationship between SOC 2 and ISO 27001 can best be seen as while ISO 27001 is not mandatory in a SOC 2 report, the completion of an ISO 27001 ISMS implementation provides (with little cost and effort) a solid basis for the preparation of the SOC 2 report. Additionally, client confidence and trust is further increased with the use of both frameworks, certified as completed within your organization.
How Interfacing Assists in Easing the Burden of SOC 2 and ISO 27001 Documentation
With the growing complexity of managing SOC 2 requirements, organizing information in a central location becomes increasingly important. When an auditor comes to site, they will assess management’s oversight of their third-party service providers as well as the company’s own controls. The majority of this oversight revolves mainly around documentation and the ability to review it. Proving this to an auditor means providing them with a record management system that can draw on the speed of access to the who, when and how’s of the organizations operations objectives.Keeping this in mind is what documentation workflow automation is all about. Creating a safe, secure and protected data ecosystem is our commitment to seeing your organization meet a successful SOC 2 or ISO 27001 certification.
Why Choose Interfacing?
With over two decades of AI, Quality, Process, and Compliance software expertise, Interfacing continues to be a leader in the industry. To-date, it has served over 500+ world-class enterprises and management consulting firms from all industries and sectors. We continue to provide digital, cloud & AI solutions that enable organizations to enhance, control and streamline their processes while easing the burden of regulatory compliance and quality management programs.
To explore further or discuss how Interfacing can assist your organization, please complete the form below.

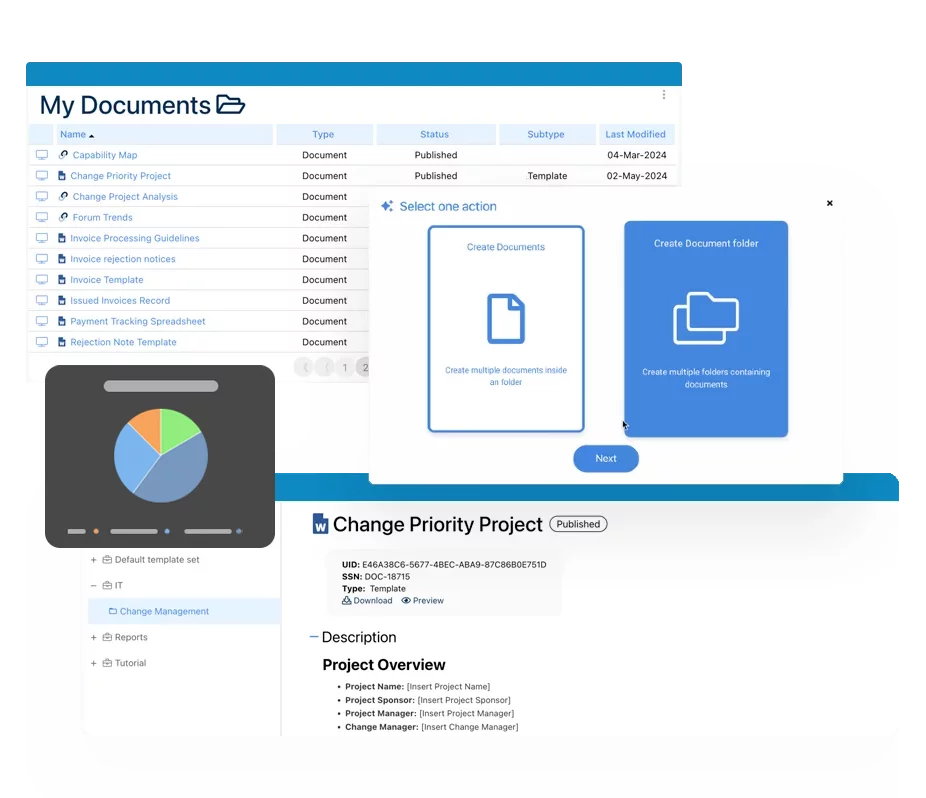
Documentation: Driving Transformation, Governance and Control
• Gain real-time, comprehensive insights into your operations.
• Improve governance, efficiency, and compliance.
• Ensure seamless alignment with regulatory standards.

eQMS: Automating Quality & Compliance Workflows & Reporting
• Simplify quality management with automated workflows and monitoring.
• Streamline CAPA, supplier audits, training and related workflows.
• Turn documentation into actionable insights for Quality 4.0

Low-Code Rapid Application Development: Accelerating Digital Transformation
• Build custom, scalable applications swiftly
• Reducing development time and cost
• Adapt faster and stay agile in the face of
evolving customer and business needs.
AI to Transform your Business!
The AI-powered tools are designed to streamline operations, enhance compliance, and drive sustainable growth. Check out how AI can:
• Respond to employee inquiries
• Transform videos into processes
• Assess regulatory impact & process improvements
• Generate forms, processes, risks, regulations, KPIs & more
• Parse regulatory standards into requirements

Request Free Demo
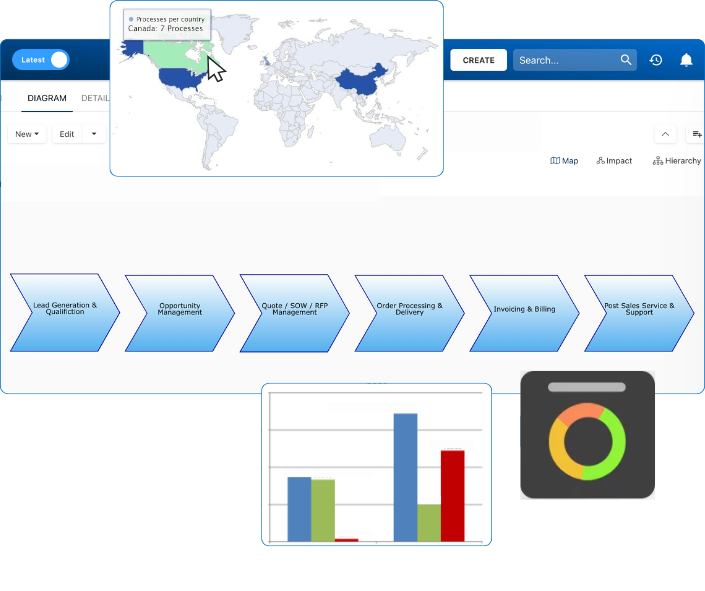
Document, analyze, improve, digitize and monitor your business processes, risks, regulatory requirements and performance indicators within Interfacing’s Digital Twin integrated management system the Enterprise Process Center®!
Trusted by Customers Worldwide!
More than 400+ world-class enterprises and management consulting firms