- Business Process Management (BPM)Document Management System (DMS)Electronic Quality Management System (QMS)Risk, Governance & Compliance (GRC)Low Code Rapid Application Development (LC)Business Continuity Management (BCM)Enterprise Architecture (EA)Business Process Management (BPM)Document Management System (DMS)
- Document Control Overview
- AI Content Creation & Improvement
- Policy & Procedure Management (SOP)
- AI Content Mining Parser
- Collaboration & Governance
- Data Migration & Integration
- Interfacing Offline App
 Electronic Quality Management System (QMS)
Electronic Quality Management System (QMS)- Quality Management System Overview
- Document Control & Records Management
- Audit & Accreditation Management
- Corrective & Preventative Action
- Quality Event (Non-conformity / Complaint/ Compliance)
- Risk Management
- Incident Management
- Environmental Health & Safety
- Product & Supplier Management (SCAR)
- Training Management
- Control Management
- Action Items Management
- Management Review
- FMEA
- Pharmacovigilance
- Data Migration & Integration
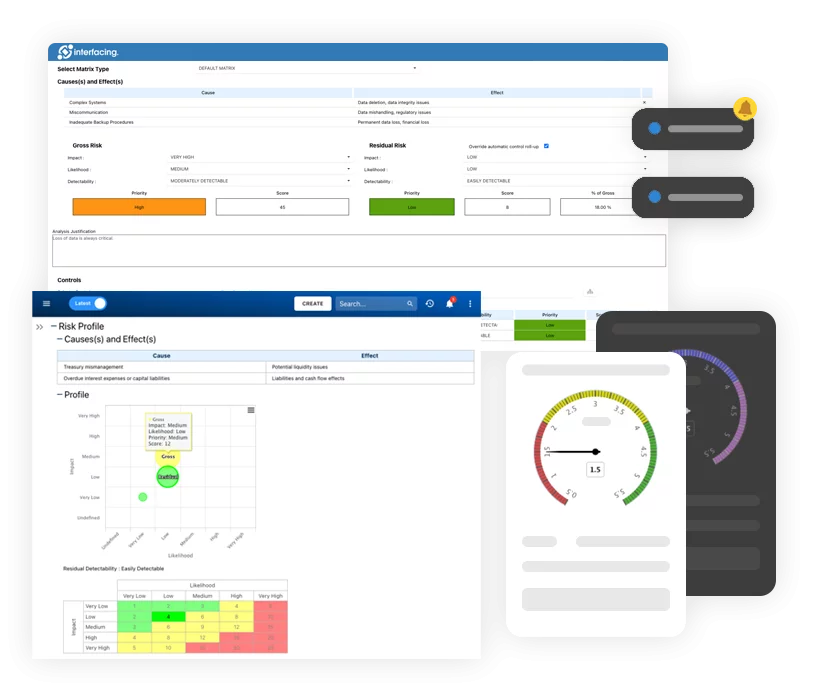
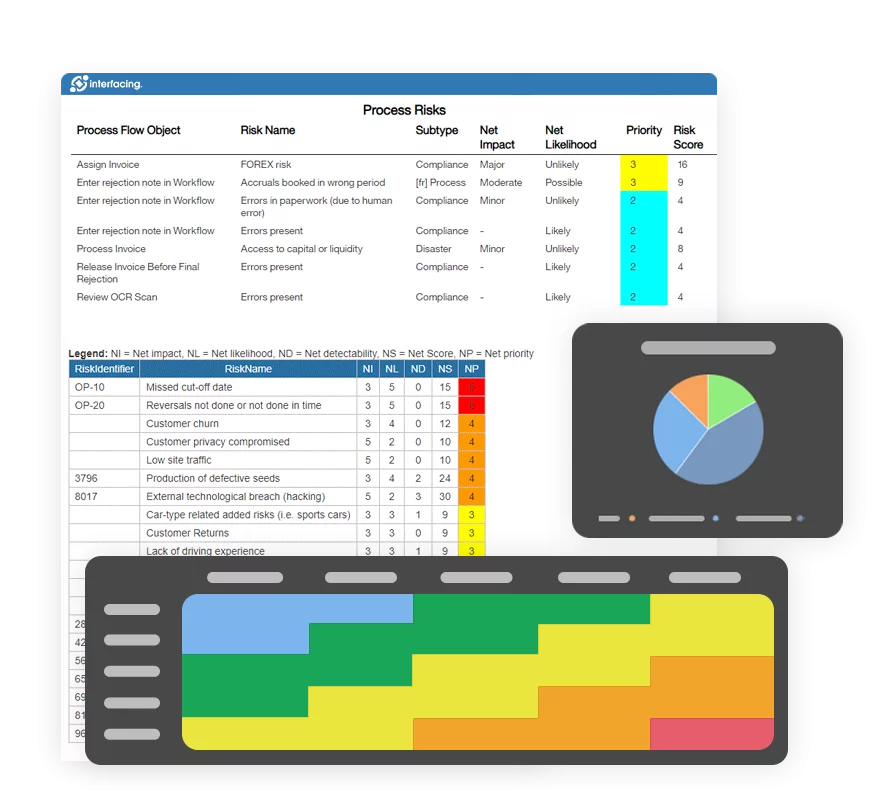
 Risk, Governance & Compliance (GRC)
Risk, Governance & Compliance (GRC)- Risk, Governance & Compliance Overview
- Risk & Control Management
- Regulatory Compliance
- Collaboration & Governance
- Data Migration & Integration
- Interfacing Offline App
 Low Code Rapid Application Development (LC)
Low Code Rapid Application Development (LC)- Low Code Automation Platform Overview
- Electronic Web Form Design (eFORMS)
- Database Table Entity Designer
- System Integration Designer
- Design & Manage Tasks
- Design & Manage BPMS Apps
- Custom Rules/Guards/Actions
- Electronic Services
- User Homepage
- BAM (Business Activity Monitoring)
- Custom Dashboard Design
- Data Migration & Integration
 Business Continuity Management (BCM)
Business Continuity Management (BCM)- Business Continuity Management Overview
- Business Impact Analysis
- Disaster Recovery Simulation
- Action Item Management
- Mass Notification Management
- Asset Management
- Interfacing Offline App
 Enterprise Architecture (EA)
Enterprise Architecture (EA) - IndustriesRegulatory ComplianceUse CasesLearning CenterFramework & PracticesIndustries
- Healthcare
- Medical Device Technology
- Life Science, Pharmaceutical
- Aerospace & Defense
- Airlines and Aviation
- Media & Telecommunications
- Government and Military
- Technology
- Energy
- Logistics & Port Operations
- Banking & Capital Markets
- Retail & Consumer
- Consulting
- Education
- Engineering & Construction
- Manufacturing
- Financial Services
- Insurance
- Chemicals
Regulatory Compliance- Regulatory Compliance
- ISO
- ISO 9001 (guide)
- ISO 9001:2026 (preparation)
- ISO 17025
- ISO 27000
- ISO 27001
- ISO27002
- ISO 42001
- EU AI Act
- SOC 2 Type 1 & 2
- Sarbanes Oxley
- GxP
- GRC
- Basel
- Digital Signature
- GDPR
- IFRS
- NIST SP 800-53
 Use Cases
Use Cases- Quality Management System (QMS)
- Digital Transformation
- Continuous Improvement
- Governance, Risk & Compliance
- Knowledge Management
- System Deployment (ERP, CRM…)
 Learning CenterFramework & Practices
Learning CenterFramework & Practices - AboutCustomer SuccessPartners

What is SOC 2?
Please Select contact form.
Definition and Use

Lesser known as the longer version, “Systems and Organizations Controls 2”, SOC 2 (or SOC II) is a framework used to assist companies demonstrate security controls that are in place to protect customer data in the cloud. These controls became known as the Trust Services Principles: Security, Availability, Processing Integrity, Confidentiality, and lastly Privacy.
If your organization is considering cloud solution providers then meeting SOC 2 compliance should be a minimum requirement (checkout our comparison of SOC1 / SOC2 /SOC3 and our comparison of SOC 2 with ISO27001 blogs).
SOC 2 Caveat
SOC 2 is neither a proxy for actual security best practices nor a legal requirement. It is not driven by HIPAA compliance or any other standards or regulations, though the assessments do in fact cover core departments and processes that interact with sensitive data.
External auditors perform certifications, not any governmental body or agency. There is no ‘pass / fail’ objective to the set of reports – the result is a subjective conclusion in-which only the auditor’s opinion is noted on record. Audit reports do not define SOC 2 certification as they are only attested as compliant, based on interpretation by a qualified licensed CPA.
Nonetheless, SOC 2 is significant in the world of data security and should not be underestimated.


SOC 2 Background
SOC 2 is a formal set of reports produced as the outcome of an audit. This audit is led by a CPA or a certified accountancy organization. It evolved from the Statement on Auditing Standards (SAS) 70, which was an older audit used to attest an organizations internal controls effectiveness.
It was later renamed the Statement on Standards for Attestation Engagements (SSAE) 16, and once again renamed to Systems and Organizations Control 1 (SOC 1). SOC 2 came about in 2009 as there was a need to have a much stricter focus on security (the five Trust Principles).
Nonetheless, SOC 2 is significant in the world of data security and should not be underestimated.


What is Trust Service Criteria (TSC)
The five quasi-overlapping categories that work toward the controls used in the SOC 2 reports are:
Security
Clearly defines that all Systems and Information remain protected against risks that would compromise integrity and impact the organizations’ ability to achieve the objectives outlined.
Availability
The Systems and Information must always be available anytime they are required in order for an organization to meet and maintain their objectives.
Processing Integrity
Any processing by the System must only provide trustworthy information at all times when requested / authorized so an organization can meet objectives.
Confidentiality
In order for an organization to meet its objectives, information can only be accessed by authorized personnel.
Privacy
personal information must be managed (protected and/or stored) in a certain way that permits the organization to meet objectives.
Who should look to SOC 2 as an organization
Any organization that stores customer data on the cloud should look to SOC 2 as a demonstration of the security roles they use to protect customer data. In effect, any SaaS company can use SOC 2 as a minimum attestation of compliance.
SOC 2 and compliance
The importance of SOC 2 compliance means that looking from the viewpoint of any customer working with a potential vendor who is SOC 2 compliant gives them a guarantee of sorts. The customer will receive the assurances and information they need on how the vendor processes user data and keeps it private. And it goes a step further. The AICPA reports also play an important role in the following:
- Regulatory oversight
- Vendor management
- Risk management process and internal corporate governance
SOC 2 Types
In the big picture, compliance to SOC 2 takes about six months with third-party assessors completing two separate audits. The SOC 2 Type 1 audit looks at the design and is a snapshot of your security processes in place at that point of time. SOC 2 Type 2 audit on the other hand, will verify your internal controls for operational effectiveness over the longer term. You must complete Type 1 as a prerequisite for Type 2 attestation. Explore our comparison of SOC1 / SOC2 / SOC3.
SOC 2 Type 1
- Form a multidisciplinary team
- Elect executive sponsor
- Identify the author who collaborates with team leads to form policies from business needs provided
- Use the Trust Services Principles as your guide
- Select those that apply to your business
- Define the scope of the audit, write/refine the policies
A SOC 2 Type 1 report will be generated after any clarifications to necessary exceptions were made.
SOC 2 Type 2
- SOC 2 Type 1 report is complete
- Verification over time that all policies and processes listed in SOC 2 Type 1 are in continuous use
For example, if a company has a very diverse and extensive cybersecurity and IT infrastructure, the audit process will likely take more time than usual for a complete SOC Report. Other factors affecting the audit scope such as the kind, location and number of users in the company (i.e. on-site and offsite) will greatly impact the attestation process.
Ultimately though the primary factor affecting the timeline to complete the SOC 2 process is incumbent upon the Type of SOC 2 report your company has selected.
SOC 2 Final Audit Report Content
The SOC 2 report content should cover the following:
- Management Assertion – ensure that management confirmation is obtained that all systems related to the services provided are described accurately and fairly in the report
- Auditor’s report – includes a summary of all tests performed as well as the results including the auditor’s opinion about the effectiveness of the controls against (when mapped to) the Trust Services Criteria
- Overview of Systems – Description in detail of the service or system reviewed.
- Trust Service Criteria Applicability – describes all controls in place including the effectiveness of those controls when Trust Service Criteria is considered.


SOC 2 and Certification
Critical to SOC 2 certification is an organizations compliance to the Trust Services Criteria as explained above (Security, Availability, Processing Integrity, Confidentiality, and Privacy).
Not every organization will complete all five principles as many companies will have criteria that is not relevant to their particular business. What is important though is that the organization chooses the correct principles in their application for SOC 2 certification that meets the scope of the audit.
Let’s look at an example. Your data center only offers storage to customers for a specific client as the client handles all data processing on their end. In this scenario, the security and availability principle applies but not the processing integrity principle. Additionally, if that storage data involves personal information, then the privacy principle would also apply.


ISO 27001 and SOC 2 working together
Check out our comparison of ISO 27001 and SOC2 and our comparison of SOC1 / SOC2 /SOC3
We shouldn’t be asking which of the two frameworks to use simply because SOC 2 is an audit report while ISO 27001 was designed as a standards certification established to create a specific Information Security Management System. This means that SOC 2 can be seen as an output brought on by the delivery of an ISO 27001 ISMS implementation.
The relationship between SOC 2 and ISO 27001 can best be seen as while ISO 27001 is not mandatory in a SOC 2 report, the completion of an ISO 27001 ISMS implementation provides (with little cost and effort) a solid basis for the preparation of the SOC 2 report. Additionally, client confidence and trust are further increased with the use of both frameworks, certified as completed within your organization.


How Interfacing Assists in Easing the Burden of SOC 2 and ISO 27001 Documentation
With the growing complexity of managing SOC 2 requirements, organizing information in a central location becomes increasingly important. When an auditor comes to site, they will assess management’s oversight of their third-party service providers as well as the company’s own controls. The majority of this oversight revolves mainly around documentation and the ability to review it. Proving this to an auditor means providing them with a record management system that can draw on the speed of access to the who, when and how’s of the organizations operations objectives.
Keeping this in mind is what documentation workflow automation is all about. Creating a safe, secure and protected data ecosystem is our commitment to seeing your organization meet a successful SOC 2 or ISO 27001 certification.
Why Choose Interfacing?
With over two decades of AI, Quality, Process, and Compliance software expertise, Interfacing continues to be a leader in the industry. To-date, it has served over 500+ world-class enterprises and management consulting firms from all industries and sectors. We continue to provide digital, cloud & AI solutions that enable organizations to enhance, control and streamline their processes while easing the burden of regulatory compliance and quality management programs.
To explore further or discuss how Interfacing can assist your organization, please complete the form below.

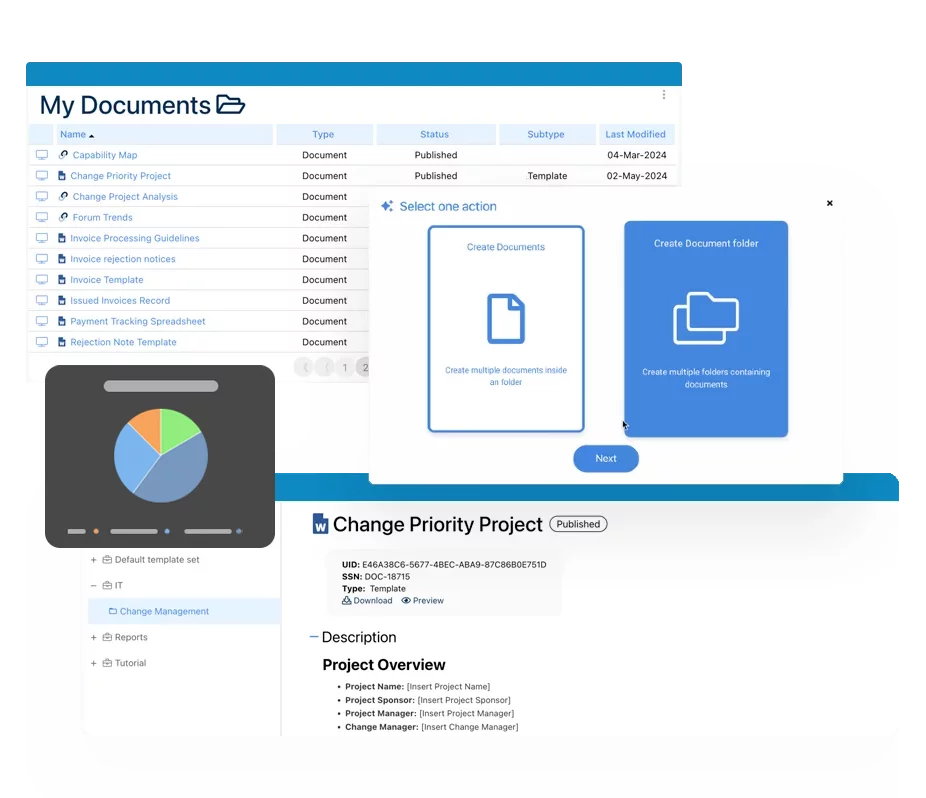
Documentation: Driving Transformation, Governance and Control
• Gain real-time, comprehensive insights into your operations.
• Improve governance, efficiency, and compliance.
• Ensure seamless alignment with regulatory standards.

eQMS: Automating Quality & Compliance Workflows & Reporting
• Simplify quality management with automated workflows and monitoring.
• Streamline CAPA, supplier audits, training and related workflows.
• Turn documentation into actionable insights for Quality 4.0

Low-Code Rapid Application Development: Accelerating Digital Transformation
• Build custom, scalable applications swiftly
• Reducing development time and cost
• Adapt faster and stay agile in the face of
evolving customer and business needs.
AI to Transform your Business!
The AI-powered tools are designed to streamline operations, enhance compliance, and drive sustainable growth. Check out how AI can:
• Respond to employee inquiries
• Transform videos into processes
• Assess regulatory impact & process improvements
• Generate forms, processes, risks, regulations, KPIs & more
• Parse regulatory standards into requirements

Request Free Demo
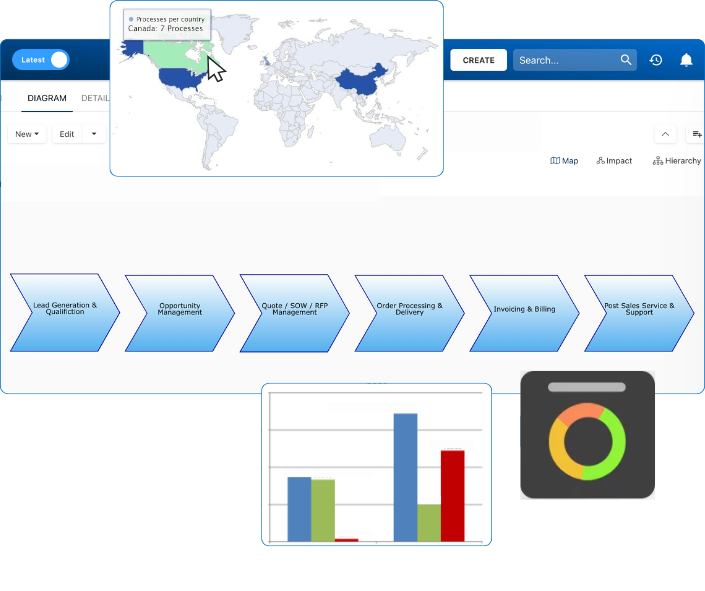
Document, analyze, improve, digitize and monitor your business processes, risks, regulatory requirements and performance indicators within Interfacing’s Digital Twin integrated management system the Enterprise Process Center®!
Trusted by Customers Worldwide!
More than 400+ world-class enterprises and management consulting firms