- Business Process Management (BPM)Document Management System (DMS)Electronic Quality Management System (QMS)Risk, Governance & Compliance (GRC)Low Code Rapid Application Development (LC)Business Continuity Management (BCM)Enterprise Architecture (EA)Business Process Management (BPM)Document Management System (DMS)
- Document Control Overview
- AI Content Creation & Improvement
- Policy & Procedure Management (SOP)
- AI Content Mining Parser
- Collaboration & Governance
- Data Migration & Integration
- Interfacing Offline App
 Electronic Quality Management System (QMS)
Electronic Quality Management System (QMS)- Quality Management System Overview
- Document Control & Records Management
- Audit & Accreditation Management
- Corrective & Preventative Action
- Quality Event (Non-conformity / Complaint/ Compliance)
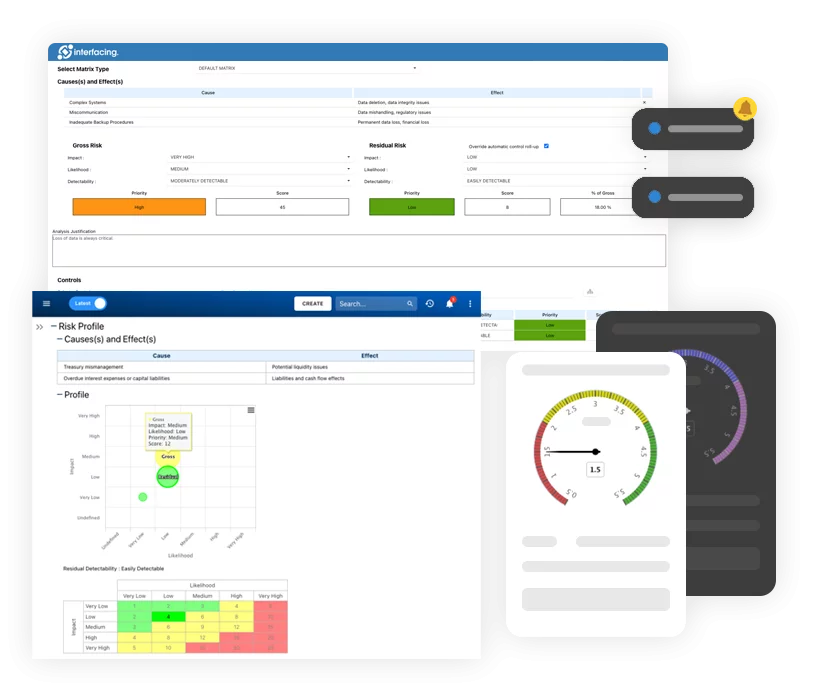
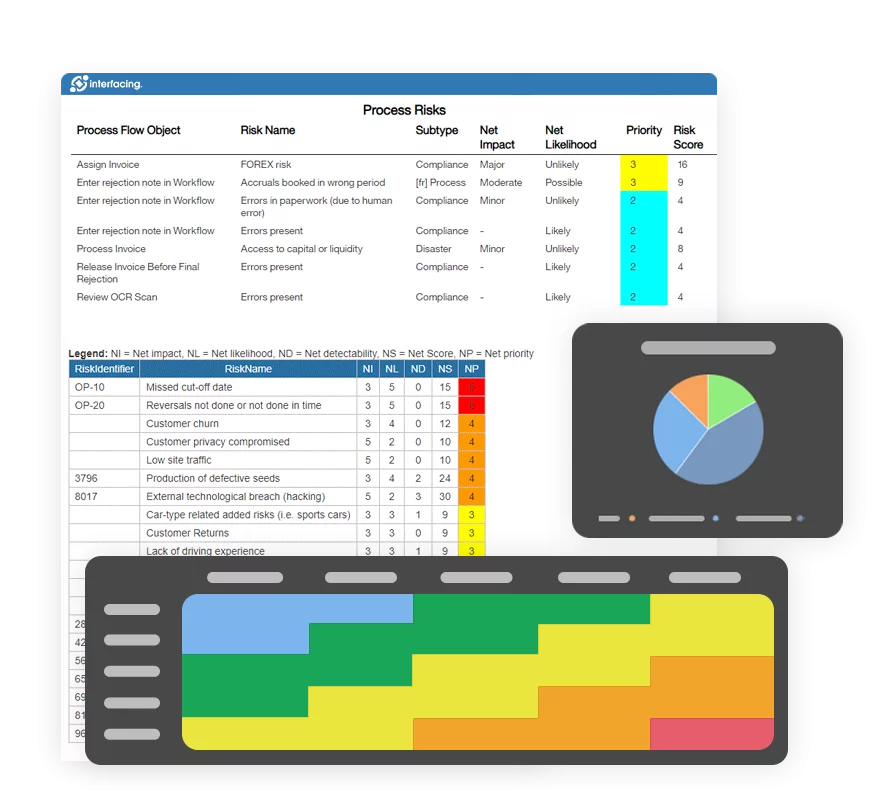
- Risk Management
- Incident Management
- Environmental Health & Safety
- Product & Supplier Management (SCAR)
- Training Management
- Control Management
- Action Items Management
- Management Review
- FMEA
- Pharmacovigilance
- Data Migration & Integration
 Risk, Governance & Compliance (GRC)
Risk, Governance & Compliance (GRC)- Risk, Governance & Compliance Overview
- Risk & Control Management
- Regulatory Compliance
- Collaboration & Governance
- Data Migration & Integration
- Interfacing Offline App
 Low Code Rapid Application Development (LC)
Low Code Rapid Application Development (LC)- Low Code Automation Platform Overview
- Electronic Web Form Design (eFORMS)
- Database Table Entity Designer
- System Integration Designer
- Design & Manage Tasks
- Design & Manage BPMS Apps
- Custom Rules/Guards/Actions
- Electronic Services
- User Homepage
- BAM (Business Activity Monitoring)
- Custom Dashboard Design
- Data Migration & Integration
 Business Continuity Management (BCM)
Business Continuity Management (BCM)- Business Continuity Management Overview
- Business Impact Analysis
- Disaster Recovery Simulation
- Action Item Management
- Mass Notification Management
- Asset Management
- Interfacing Offline App
 Enterprise Architecture (EA)
Enterprise Architecture (EA) - IndustriesRegulatory ComplianceUse CasesLearning CenterFramework & PracticesIndustries
- Healthcare
- Medical Device Technology
- Life Science, Pharmaceutical
- Aerospace & Defense
- Airlines and Aviation
- Media & Telecommunications
- Government and Military
- Technology
- Energy
- Logistics & Port Operations
- Banking & Capital Markets
- Retail & Consumer
- Consulting
- Education
- Engineering & Construction
- Manufacturing
- Financial Services
- Insurance
- Chemicals
Regulatory Compliance- Regulatory Compliance
- ISO
- ISO 9001 (guide)
- ISO 9001:2026 (preparation)
- ISO 17025
- ISO 27000
- ISO 27001
- ISO27002
- ISO 42001
- EU AI Act
- SOC 2 Type 1 & 2
- Sarbanes Oxley
- GxP
- GRC
- Basel
- Digital Signature
- GDPR
- IFRS
- NIST SP 800-53
 Use Cases
Use Cases- Quality Management System (QMS)
- Digital Transformation
- Continuous Improvement
- Governance, Risk & Compliance
- Knowledge Management
- System Deployment (ERP, CRM…)
 Learning CenterFramework & Practices
Learning CenterFramework & Practices - AboutCustomer SuccessPartners

What is ISO 27002:2022
Please Select contact form.
The Essential Framework for Safeguarding Sensitive Data

An introduction to ISO27002:2022
ISO/IEC 27002:2022 is an update to the previously published ISO/IEC 27002:2013 standard. This information security standard reference is used to support ISO 27001. This standard is published by the International Organization for Standardization (ISO) and the International Electrical Commission (IEC). ISO 27002 is closely associated with ISO 27001 as a supporting set of controls used for ISMS and how organizations may choose to implement them.
It is important to note that ISO 27002 is not a certifiable standard by itself. It acts as a point of reference for information security, cyber security and privacy protection controls that are based on internationally recognized standards of best practices for organizations planning on ISO 27001 certification.
ISO 27002 controls can be found in Annex A of ISO/IEC 27001. This is the section most information security experts will refer to when the topic of security controls is discussed. It’s important to note that while the outline of each control in Annex A is only a few sentences, ISO 27002 refers to each control with an average of one page per each. This is simply because the ISO 27002 standard must explain how each control works, what is the objective of said control, and how that particular control can be implemented.
ISO 27002:2022 Update
Drastic changes were made to this ISMS framework structure in February of 2022, replacing the previous published release from 2013. Despite the structural modifications the documents purpose remains the same; providing a generic reference set of information security controls used within the context of ISO 27001 Information Security Management System (ISMS).


Key Updates – ISO 27002:2022
14 Categories Reduced to 4 Domains
- A.5 Organizational Controls
- A.6 People Controls
- A.7 Physical Controls
- A.8 Technological Controls
Additionally, there are 2 annexes referenced:
- Annex A – Using attributes
- Annex B – Correspondence with ISO/IEC 27002:2013
The ultimate impact of ISO 27002 is in its contribution to the stability of and organizations ISMS. A key difference is that ISO 27002 is not intended to distinguish between applicable controls used or not within an organization. ISO 27002 is to be used as a reference for the selection of security controls rather than a certification process.
Security control reduction due to consolidation
With the consolidation of controls in ISO 27002, the number of security controls is now reduced to 93 from 114. Specifically, out of the 93 controls, 58 were updated, 24 were merged and 11 new controls we created.
Eleven new controls overview
While already referenced across multiple controls, the latest version of ISO 27002 gave these topics a more focused detail and guidance in their own control.

Of the eleven controls, there are three that are most impactful:
- 7 – Threat intelligence: Keeping your organization secure is only possible by identifying threat possibilities. Only by doing this will you be able to calculate any risks posed to the company and implement measures to mitigate the risk. This organizational control offers guidance to the collection and analysis of data regarding threats to information security. Consideration is given to the strategy, tactical implementation and operations of threat intelligence.
- 23 – Information security for use of cloud services: Organizations are migrating to cloud services at an ever-increasing rate. As a consequence of this pace, most companies make the assumption that security risk identification and control is the responsibility of the cloud service provider. This, however, is not often the case. This control provides guidance for the acquisition, use, management and exit from third-party cloud services. It clearly states that your organization must define in detail, the responsibilities of both your organization and your cloud service provider.
- 28 – Secure coding: As companies are constantly increasing that develop software, poorly coded sections can result in major vulnerabilities. For example, an absence of validation of input parameters can lead to SQL injections, XSS attacks etc. The technical control guidance provided here ensures secure coding principles that should be applied in software development.

Attribute values introduced for controls
The final major change introduces five attributes, including values for each.
- Cybersecurity concepts: #Identify, #Protect, #Detect, etc.
- Information Security Properties: #Confidentiality, #Integrity and #Availability
- Security domains: #Governance_and_Ecosystem, #Protection, #Defense, etc.
- Control types: #Preventive, #Detective and #Corrective
- Operational capabilities: #Governance, #Asset_management, #Information_protection, etc.
Now when referencing Annex A, attributes will link one or more values from each attribute to any of the security controls. Easier grouping and sorting are the result of this change. As an example, if an organization wishes to strengthen preventative controls, filtering using the #preventative value in the attribute Control types will present a list of preventative control references.
Annex B in this version remains retroactive to ISO/IEC 27002:2013 and allows for an easy transition to ISO 27002s updated version.
ISO 27002 changes and its impact on your organization
When planning out your ISO 27001 information security management system project, it would be safe to assume that both ISO 27001 and ISO 27002 would be the cornerstone of your ISMS. Using the security controls included in the new ISO 27002 will result in alignment to the current industry best practices. Your infrastructure may benefit more as a result of the new introductions as a strengthened integration to existing frameworks, regulations or standards.
How Interfacing can Help Ease the Burden of
ISO/IEC 27002:2022 Documentation
With the growing complexity of managing ISO 27000 series requirements, organizing information in a central location becomes increasingly important. When an auditor comes to site, they will assess management’s oversight of their third-party service providers as well as the company’s own controls. The majority of this oversight revolves mainly around documentation and the ability to review it. Proving this to an auditor means providing them with a record management system that can draw on the accuracy & speed of access to the who, when and how’s of the organizations operations objectives.
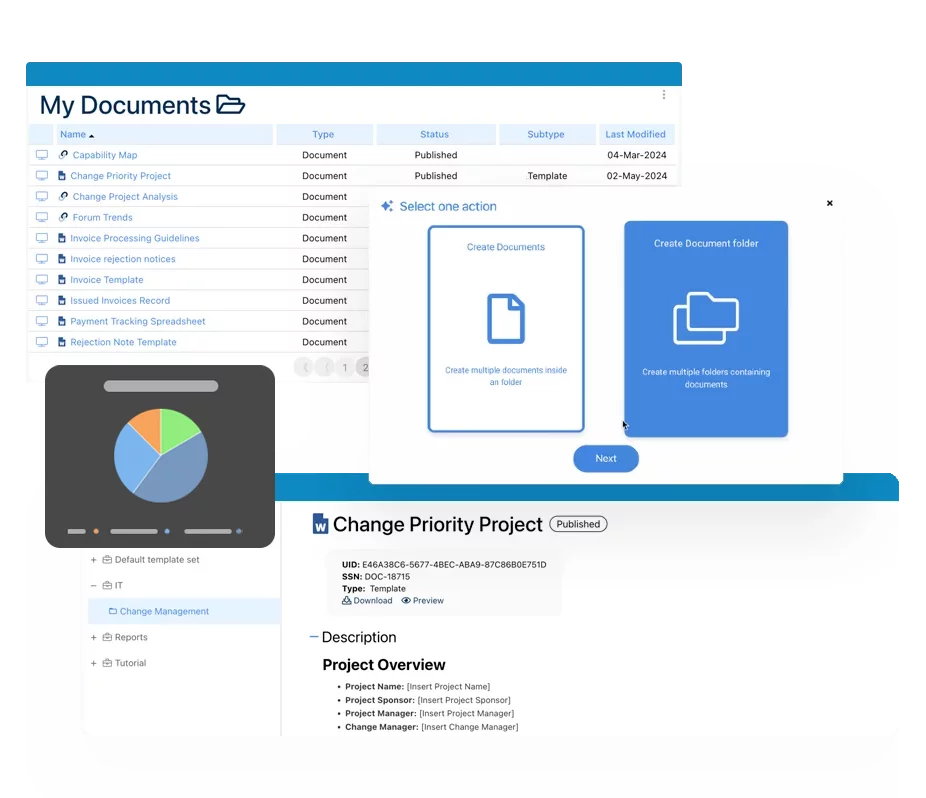
Interfacing’s Enterprise Process Center® digital platform solution maintains a complete library of:
- Processes
- Procedures
- Roles & responsibilities
- Risks
- All requirements
- Internal policies
- Aligned indicators (KPIs)
- Controlled indicators (Monitoring)
All of the above within a centralized Integrated Management System (IMS), allowing your organization to fast-track certification and simplify creation, communication (new & changes) and update of information security controls, processes and associated/related documentation.
Additionally Interfacing’s IMS also offers a Quality Management System for automating the training of your different controls and audits (action item management/CAPA) as well as managing all your documentation, files, processes, procedures, roles, risks & controls.
We offer an entire library of content to jump start your program or use as a reference library for the operating controls used to validate the maturity of your current ISO 27001 documentation.
Why Choose Interfacing?
With over two decades of AI, Quality, Process, and Compliance software expertise, Interfacing continues to be a leader in the industry. To-date, it has served over 500+ world-class enterprises and management consulting firms from all industries and sectors. We continue to provide digital, cloud & AI solutions that enable organizations to enhance, control and streamline their processes while easing the burden of regulatory compliance and quality management programs.
To explore further or discuss how Interfacing can assist your organization, please complete the form below.

Documentation: Driving Transformation, Governance and Control
• Gain real-time, comprehensive insights into your operations.
• Improve governance, efficiency, and compliance.
• Ensure seamless alignment with regulatory standards.

eQMS: Automating Quality & Compliance Workflows & Reporting
• Simplify quality management with automated workflows and monitoring.
• Streamline CAPA, supplier audits, training and related workflows.
• Turn documentation into actionable insights for Quality 4.0

Low-Code Rapid Application Development: Accelerating Digital Transformation
• Build custom, scalable applications swiftly
• Reducing development time and cost
• Adapt faster and stay agile in the face of
evolving customer and business needs.
AI to Transform your Business!
The AI-powered tools are designed to streamline operations, enhance compliance, and drive sustainable growth. Check out how AI can:
• Respond to employee inquiries
• Transform videos into processes
• Assess regulatory impact & process improvements
• Generate forms, processes, risks, regulations, KPIs & more
• Parse regulatory standards into requirements

Request Free Demo
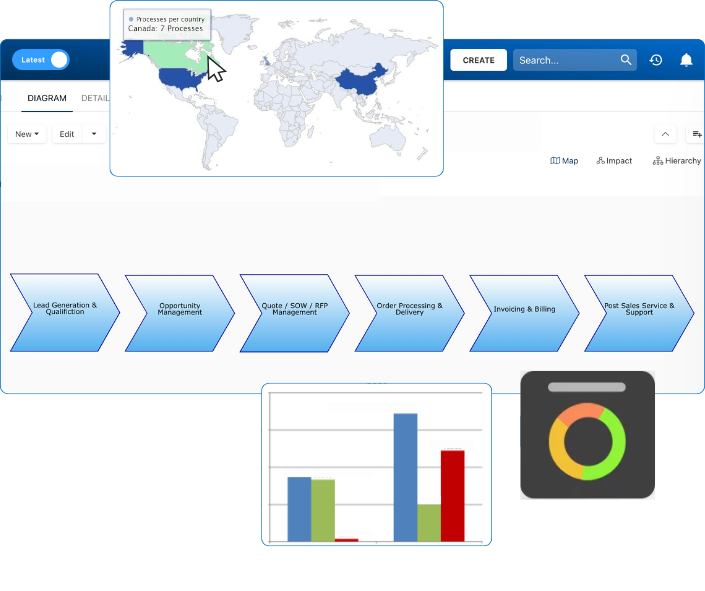
Document, analyze, improve, digitize and monitor your business processes, risks, regulatory requirements and performance indicators within Interfacing’s Digital Twin integrated management system the Enterprise Process Center®!
Trusted by Customers Worldwide!
More than 400+ world-class enterprises and management consulting firms