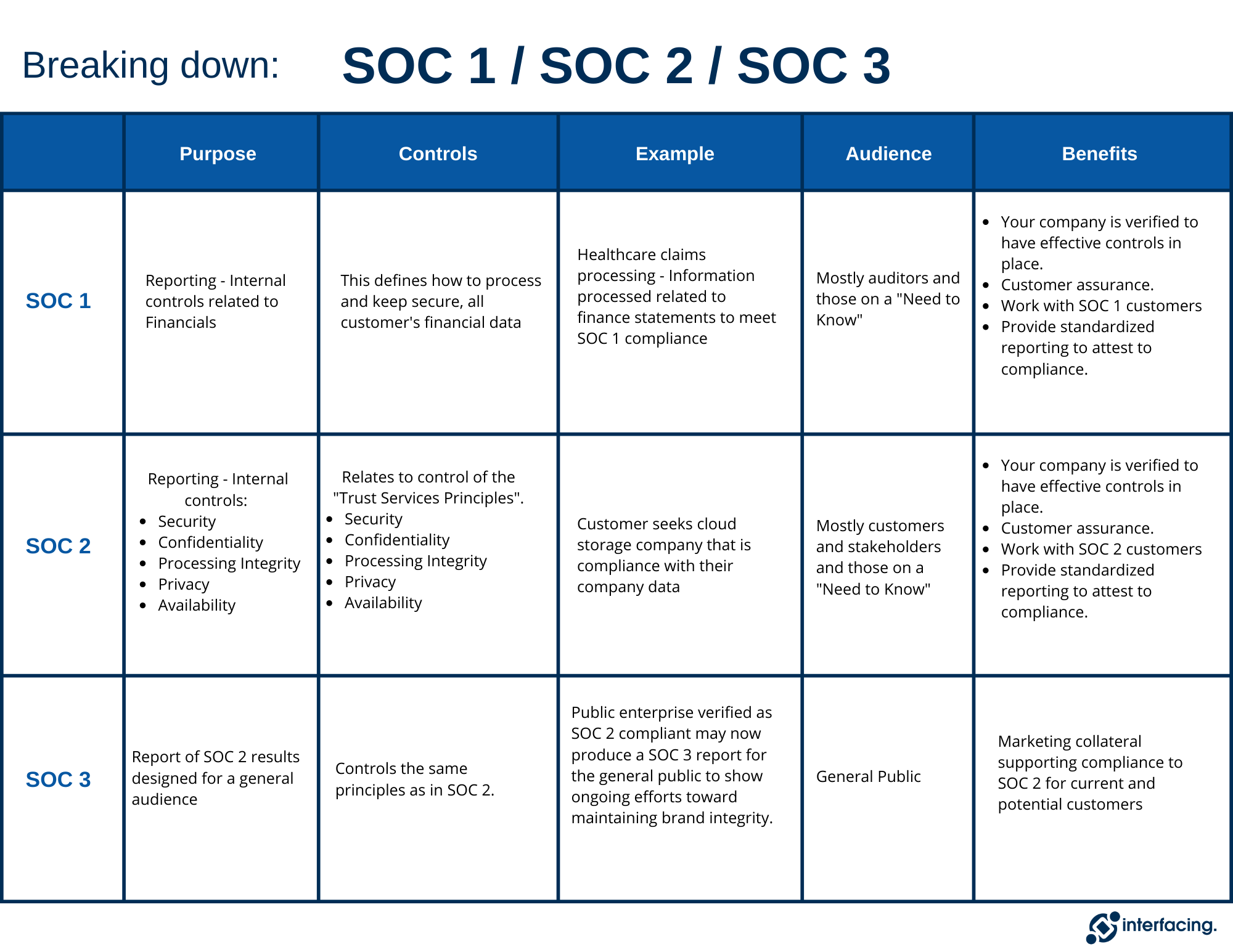
Comparing – SOC 1 / SOC 2 / SOC 3
Summary
- SOC 1 – Used for Compliance Reporting (private to the company) – Internal controls related to Financials
- SOC 2 – Used for Compliance Reporting (private to the company) – Internal controls related to:
- Security
- Confidentiality
- Processing Integrity
- Privacy
- Availability
- SOC 3 – Used for Compliance Reporting of SOC 2 results designed for a general (public) audience
Compliance to certain standards builds integrity and trust throughout the journey of your business’s expansion. Learn the distinctions between SOC 1, SOC 2, and SOC 3 compliance below.
SOC stands for “Service Organization Control,” and that sentence sums up what it’s all about: In essence, you are a “service organization,” and to be considered SOC-compliant, you must demonstrate that you have specific controls in place.
Because most businesses can’t or won’t utilize your services without it, SOC compliance is crucial. You cannot secure the enterprise transactions that will keep your organization viable without SOC compliance. The definitions of SOC 1, SOC 2, and SOC 3, as well as the distinctions between them, are discussed in this article. When it’s all said and done, you’ll know which is essential and which is required, and you’ll also learn how to start along the road to compliance.
Overview of SOC 1 / SOC 2 / SOC 3
SOC compliance proves that your clients may depend on the services you offer. Your business is audited by an accountant, who then certifies you with a SOC report to share with your clients.
This report demonstrates your reliability. But knowing when to seek SOC compliance and what kind of SOC report to get requires a deeper understanding of SOC compliance. So let’s simplify it even more.
The Main Distinctions Between SOC1, SOC2, and SOC3
The first two of the three main SOC reports are the most common (i.e., SOC 1 & SOC 2), and the second is the one that concerns technology businesses the most.
The most typical SOC reports are SOC 1 and SOC 2; thus, it’s crucial to comprehend their distinctions. SOC 1 and SOC 2 differ in that SOC 1 is more concerned with financial reporting, whereas SOC 2 is more concerned with compliance and operations.
Reports from SOC 3 are less frequent. SOC 3 is a variation of SOC 2 and has the same data as SOC 2, but it is presented for a lay audience as opposed to an informed one. SOC 3 is intended for the company’s clients, whereas SOC 2 is intended for auditors and internal stakeholders of the company you are selling to.
Other SOC reports include a few that are less common and outside the purview of this article:
- SOC for Cybersecurity provides information on how well a service organization manages its cybersecurity risk.
- SOC for Supply Chain provides information on how well a service company manages supply chain risk.
How to Become SOC-compliant
You must collaborate with an independent CPA in order to become compliant and obtain a SOC report. The breadth, design, and/or operational efficacy of your internal control processes are evaluated by a separate CPA. The SOC report’s scope will be decided jointly by you and your CPA.
The last word belongs to the AICPA. It’s not one of those situations right now when you can act quickly and break stuff. Your business will be audited by a CPA or CPA firm.
Once any gaps in your controls have been closed, they will certify you as SOC (1 or 2)-compliant. When you present your clients with this SOC report, they will believe it because it is standardized and can only be produced by qualified experts. There are several reasons why you might want to adopt SOC best practices. The fact that many of your clients will audit all the services they use on an annual basis is foremost among them.
The volume of these audits will increase as your business expands and becomes onerous. Instead of dealing with individual audits, you can produce a SOC report if you become SOC-compliant.
You can be sure that neither do your clients, who don’t want to be subjected to individual audits. Many businesses, particularly the larger ones, will genuinely object. It’s SOC or nothing to them. You desire those bargains; we’re sure of it.
- Service Organization Control is referred to by the abbreviation SOC
- SOC report: A report that notifies your clients of the internal security measures you have implemented. Its goal is to assist clients in evaluating the risks associated with employing an outsourced service
- SOC compliance is standardized by the American Institute of Certified Public Accountants (AICPA)
- Licensed and registered accountants who can provide SOC 1, 2 and 3 reports are known as Certified Public Accountants (CPAs)
- Control: A control is a measure taken to either achieve or prevent an undesirable event
- A business that makes use of a service provider is a user entity
- A business that provides information system services to other businesses is a service organization. Data centers managed IT services, SaaS vendors, and other topics are discussed (i.e., you)
- A user entity representative who examines the SOC report is an auditor(s)
- Statement on Auditing Standards (SAS-70): There have been numerous SAS-70s. There were a few issues prior to SAS-70, but the 70th release caused confusion. AICPA issued SSAE No. 16 to provide clarification
- Statement on Standards for Attestation Engagements, or SSAE No. 16 and SSAE No. 18, are acronyms that none of these terms will be used in this article (breathe a sigh of relief). Let’s say that SSAE No. 18 is where SOC 1, SOC 2, and SOC 3 are located (and it replaced the earlier house, SSAE no. 16)
What is a SOC1 Report
Financial reporting is the main focus of SOC 1. It is important to have internal controls in place and be able to demonstrate them when handling financial information about your clients. Naturally, this information is highly significant to your customers because they have to submit it to their auditors.
Why is SOC 1 compliance important?
Your business offers services to other businesses. As a result, your services might have an impact on how your clients report their financial information (something that your clients’ auditors worry a lot about). SOC 1 compliance is all about demonstrating that you have the safeguards in place to guarantee that both the service’s actual operations and its design are reliable and predictable.

SOC 1 Compliance Types
There are two different types of SOC 1 compliance reports: Type 1 and Type 2. Both types examine how your controls were specified or created as of a specific date. The main distinction is that auditors test one control in a Type 1 report to validate your description and design. The efficiency of your controls is examined in a Type 2 report during a predetermined time frame, such as six months.
SOC 1 Compliance: When to Get It
SOC 1 compliance is probably not something you’re thinking about when you initially start off. It’s crucial to time your compliance, though, since you don’t want to be rushing to get certified while a contract is on the line. The market will let you know when compliance is truly necessary, but ideally, you want to offer compliance just before you need it.
In addition to timing, the following two factors will make SOC 1 compliance necessary:
- Your customer requests a “right to audit.”
- If your business will be publicly traded, you must adhere to other relevant laws and regulations, such as the Sarbanes-Oxley (SOX) Act.
In either case, SOC 1 compliance will essentially become your top concern.
Who is concerned about SOC 1 compliance?
In general, your clients are concerned about how you handle their financial information. SOC 1 is not frequently requested or required by tech firms. When businesses do employ SOC 1, internal auditors create the SOC 1 reports, which external auditors then examine and validate. SOC 1 compliance largely stays between auditors.
SOC 1 Compliance Types
There are two different types of SOC 1 compliance reports: Type 1 and Type 2. Both types examine how your controls were specified or created as of a specific date. The main distinction is that auditors test one control in a Type 1 report to validate your description and design. The efficiency of your controls is examined in a Type 2 report during a predetermined time frame, such as six months.
SOC 1 Compliance: When to Get It
SOC 1 compliance is probably not something you’re thinking about when you initially start off. It’s crucial to time your compliance, though, since you don’t want to be rushing to get certified while a contract is on the line. The market will let you know when compliance is truly necessary, but ideally, you want to offer compliance just before you need it.
In addition to timing, the following two factors will make SOC 1 compliance necessary:
- Your customer requests a “right to audit.”
- If your business will be publicly traded, you must adhere to other relevant laws and regulations, such as the Sarbanes-Oxley (SOX) Act.
In either case, SOC 1 compliance will essentially become your top concern.
Who is concerned about SOC 1 compliance?
In general, your clients are concerned about how you handle their financial information. SOC 1 is not frequently requested or required by tech firms. When businesses do employ SOC 1, internal auditors create the SOC 1 reports, which external auditors then examine and validate. SOC 1 compliance largely stays between auditors.
What is a SOC2 Report
Particularly in relation to cloud computing and data security, SOC 2 is focused on operations and compliance. Internal controls that meet the five requirements set forth by the AICPA must exist and be able to be demonstrated. Let’s take a brief break right here. SOC 2 is the important one if you work for a tech company.
Why is SOC 2 compliance important?
Companies all around the world have been able to outsource tasks to service providers because of the cloud computing industry’s rapid expansion. This made it more difficult to ensure compliance for the clients of these businesses. Compliance with one company actually entails compliance with every company it does business with.
To meet this requirement, SOC 2 was created. SOC 2 and related rules will probably only become more significant. Although outsourcing may have started with the outsourcing of IT services, cloud computing has made it possible for any function or feature to be performed by a different company. Even with just a few lines of code, you can outsource with API-first businesses.
This rule applies to all contracted-out tasks. Outsourcing promotes focus, and entrepreneurs need attention to succeed in today’s fiercely competitive marketplaces.
SOC 2 Compliance Types
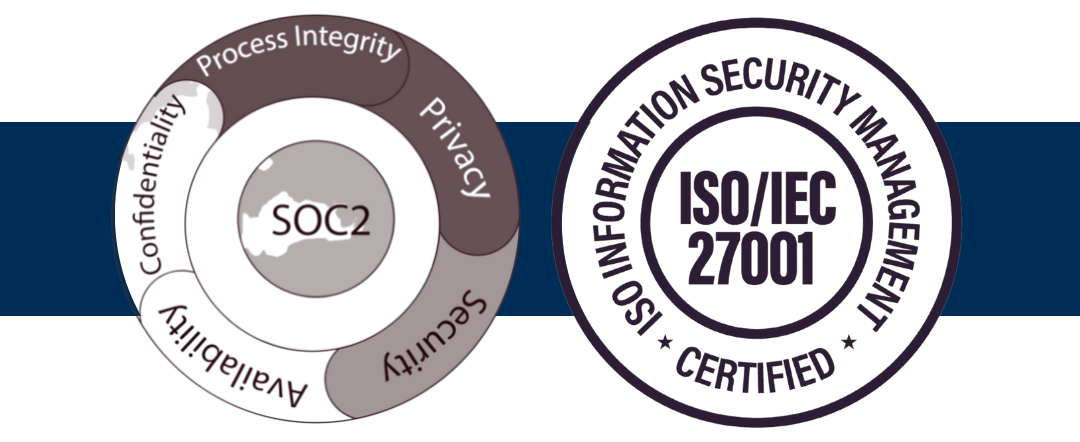
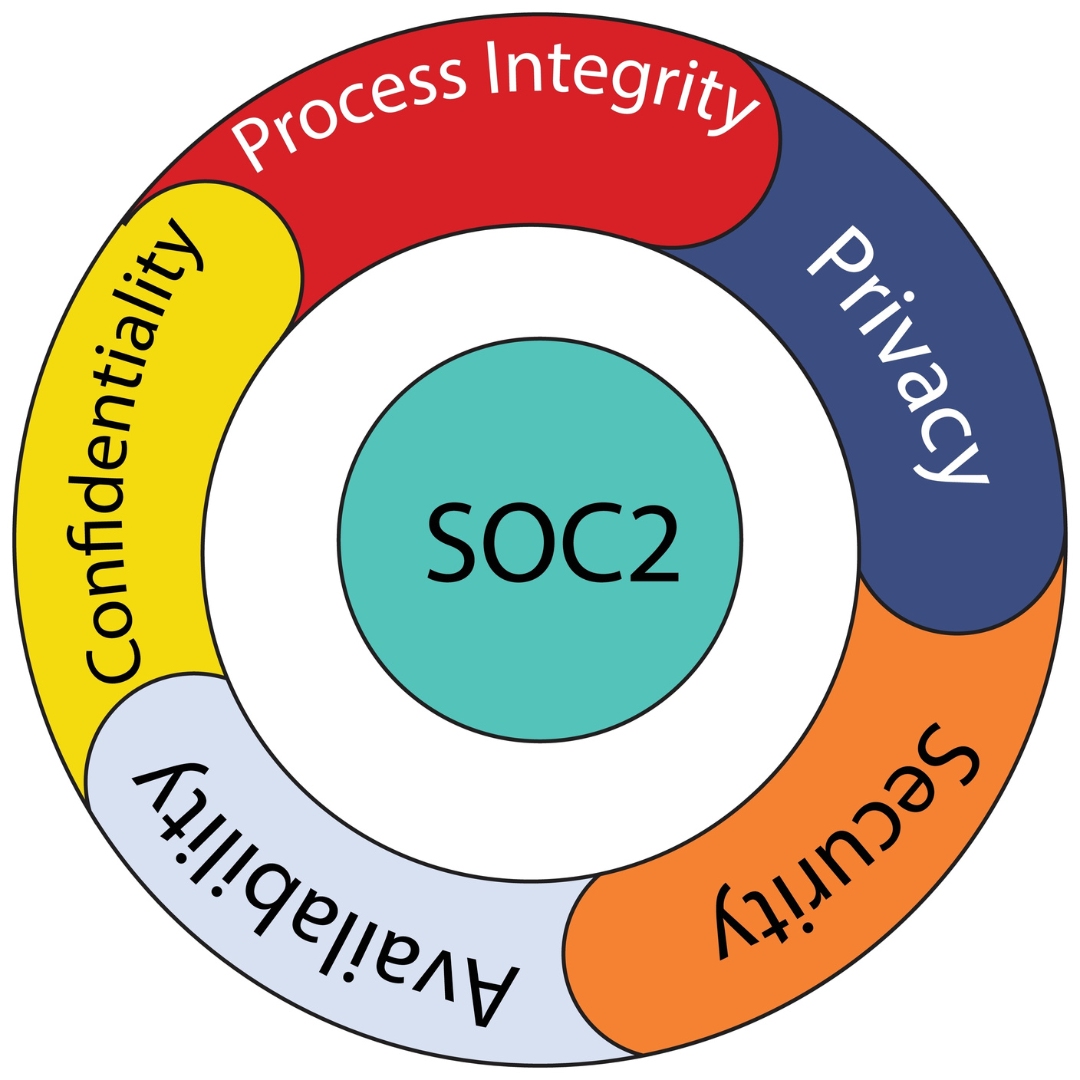
SOC 2 reports come in two different varieties, the same as SOC 1 reports. Only the scope and timeframe are different. Both sorts of reports examine how your controls were described or created as of a specific date. The main distinction is that auditors test one control in a Type 1 report to validate your description and design. The effectiveness of a service organization’s controls are examined in a Type 2 report over a predetermined time frame, such as a year. Additionally, SOC 2 compliance varies according to the scope that you and your CPA select. Five Trust Services Criteria from the AICPA are used by auditors to assess the layout and efficiency of your controls. The five requirements are:
- Security: Can you warn clients of questionable conduct, and are your systems protected from unwanted access?
- Confidentiality: Does your client limit the dissemination of sensitive information? And if so, how?
- Processing Integrity: Do your systems make sure that processes function exactly as they should?
- Privacy: Does your client limit the dissemination of personal information? And if so, how?
- Availability: Can your customers access your systems in the manner and to the extent permitted by their contracts?
The sole need is security; the rest will depend on how well it applies to your company. The integrity of your transaction processes will probably be very important to your customers if you operate an e-commerce business, for example. Your consumers will be very concerned with availability if you are offering a basic, infrastructure-level service.
SOC 2 Compliance: When to Get It
The market will tell you how urgently you require SOC 2 compliance. It is more probable that a large customer you are chasing will request to see a SOC 2 report. That being said, you should pursue SOC 2 if you handle or host non-financial data (at some point).
Additionally, keep in mind that major compliance frameworks like HIPAA and PCI-DSS do not actually mandate SOC 2. However, given the frequency of data breaches, many businesses, particularly large ones, may need to demonstrate SOC 2 compliance before finalizing a purchase. SOC 2 Type 1 and Type 2 reports are relevant in this situation as well.
Many startups will obtain Type 1 SOC compliance in an effort to seem compliant. A Type 1 report is a certification that you have controls in place at a specific moment in time. Because of this, a lot of companies may demonstrate transient compliance, assert overall SOC 2 compliance, and then pursue a Type 2 report later.
Unfortunately, the IT administrators of your potential customers are savvy and will probably not give much credence to a Type 1 report. It’s frequently wiser to go through an accelerated procedure and request a Type 2 report right away if you truly want SOC 2 compliance, which you do.
Who is concerned about SOC 2 compliance?
SOC 2 reports typically have a wider readership than SOC 1 compliance reports, where the writers and readers of the report are almost certainly both auditors. Customers, management, and regulators will all get SOC 2 reports from businesses, frequently with an NDA attached.
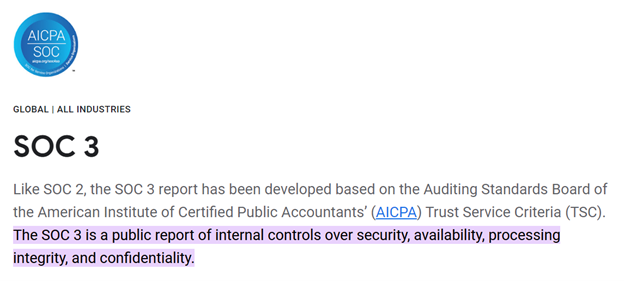
What is SOC3
The odd one out of the group is SOC 3. SOC 3 is meant to be given to a broad audience and provides the same material as SOC 2. As a result, we won’t go into as much detail. Companies frequently use SOC 3 compliance, along with a seal that confirms compliance, to post on their websites. SOC 3 reports are available for Microsoft, AWS, and Google Cloud, for instance. The SOC 3 report from Google Cloud (screenshot below) even includes a useful explanation of what SOC 2 is and entails.
Microsoft has a FAQ area that enables readers to learn more in-depth.
SOC 3 reports are mostly used by businesses as marketing tools to show how effective their internal controls are. As you can see in the image above, the AICPA seal is prominently displayed by both Google Cloud and AWS to demonstrate their compliance.
SOC 3 reports are almost complete when businesses produce their SOC 2 reports because they contain the majority of the data in a SOC 2 report. Due to this, a lot of businesses will frequently request that the auditors who created their SOC 2 report also create a summary that serves as their SOC 3. Click through to any of the SOC 3 studies we cited above if you want to learn more.
These illustrations provide templates for your SOC 3 reports and a peek into the SOC 2 reports of these businesses.
Is SOC 2 Equivalent to ISO 27001?
There are significant similarities between these two security governance frameworks. Both are optional and made to demonstrate a company’s reliability in handling consumer data while preserving its confidentiality, integrity, and accessibility. Clients perceive both of the frameworks as solid evidence of your company’s capacity to protect customer data because they both have equally well-regarded and respected reputations. Attestation vs. certification is the key distinction between the two frameworks. SOC 2 is a dual-type security control function attestation that produces a deliverable report.
The performance of an ISMS as a whole over time is more the focus of ISO 27001, which also offers certification. Both were created to make sure that appropriate security controls were there and functioning, but ISO 27001 takes it a step further by requiring that an ISMS be in place for continuous data security.
Specifically, as a comparison, ISO 27001 is a global standard defining all requirements and controls related to the systematic preservation and protection of information. This standard applies to all organizations of any size and industry. ISO 27001 is comprised of 114 security controls and 10 clauses that are grouped into 14 sections. To be more precise, the ISMS (Information Security Management System) defined in clauses (4 to 10) gives an organization the ability to keep its levels of security aligned with its ability to meet the desired objectives and outcomes of its business based on a risk management approach.
Using ISO 27001 as your company’s security management foundation, in effect means that your organization is already performing many of the activities required to achieve a successful SOC 2 audit and certification.
How Interfacing Assists in Easing the Burden of SOC 2 and ISO 27001 Documentation
With the growing complexity of managing SOC 1, SOC 2, and SOC 3 requirements, organizing information in a central location becomes increasingly important. When an auditor comes to the site, they will assess management’s oversight of their third-party service providers as well as the company’s own controls. The majority of this oversight revolves mainly around documentation and the ability to review it.
Interfacing’s IMS platform provides your organization with the ability to capture all equivalency of SOC 1 and SOC 2 requirements (and SOC 3) and match them, where necessary, to ISO international standards (such as ISO 27001 and ISO 9001). This includes running audits and testing to meet SOC compliance, as well as creating test requirements and evidence requests for your internal and external auditors.
Being compliant is just as much about proving this to an auditor as much it is about actually applying the technical controls on your organization, which means providing your auditors with a state-of-the-art quality record management system that can draw on the traceability, accuracy & speed of access to the who, when and how’s of the organizations’ operations objectives.
Interfacing’s Enterprise Process Center® digital platform solution helps you maintain a complete library of:
- Processes
- Procedures
- Roles & responsibilities
- Risks
- All regulatory requirements and standard controls
- Internal policies
- Aligned indicators (KPIs)
- Controlled indicators (Monitoring)
All of the above within a centralized Integrated Management System (IMS) allows your organization to fast-track certification and simplify the creation, communication (new & changes), and update of information security controls, processes, and associated/related documentation.
Additionally, Interfacing’s IMS also offers a Quality Management System for automating the training of your different controls and audits (Managing end-to-end from Audit findings, to CAPA, including action item management) as well as managing all your documentation, files, processes, procedures, roles, risks & controls.
We offer an entire library of content to jump-start your program or use as a reference library for the operating controls used to validate the maturity of your current ISO 27001 documentation.
The success of an enterprise deal primarily rests on how quickly it closes. The longer it goes on, the greater the chance that a crucial stakeholder may change their mind or that a rival will intervene. Prepare for SOC compliance in advance rather than rushing when your client asks.
Why Interfacing?
Interfacing’s digital Integrated Management System (IMS) provides you with a tool to control compliance by helping you manage the audit, assessment, non-conformity, CAPA, training, and execution of your underlying business processes. IMS supports control documentation, control testing, audit automation, and more to satisfy SOC 2 compliance. Ultimately, this will make compliance easier and more transparent throughout your organization.
Only our Integrated Management System will give your company the ability to automatically and continuously monitor and manage your compliance initiatives. Implementing controls associated with processes and tasks ensures that compliance requirements are followed, while automatic tracking and documentation of all process changes gives management complete oversight.
If you would like to see more or discuss how Interfacing can help your organization, be sure to click below.
Contact us more for information.
Gain Transparency with the Enterprise Process Center®
Interfacing’s Digital Twin Organization software provides the transparency and Governance to improve Quality, Efficiency and ensure Regulatory Compliance.
Read Our Blogs
Take a moment to read blogs about GXP, Regulatory Compliance, today’s trends, and much much more!
Discover how your organization benefits from an Interfacing solution.
A key differentiator of Interfacing to other digital and business transformation consulting firms is that Interfacing offers its own innovative technology solution in support of transformation programs. Interfacing’s software solutions deliver the transparency required to reduce complexity, improve execution and facilitates agility and change.
Interfacing’s Integrated Management System is a one-stop-shop for managing transformation programs. We know it’s a very competitive environment out there. It is for that reason our strength is in our commitment to maintain flexibility throughout the project lifecycle whether it is in our innovative products or in our team of experts.
Try It Now For Free!
Document, improve, standardize, and monitor your business processes, risks and performance with Interfacing’s Business Process Management Software (BPM Software) the Enterprise Process Center®!